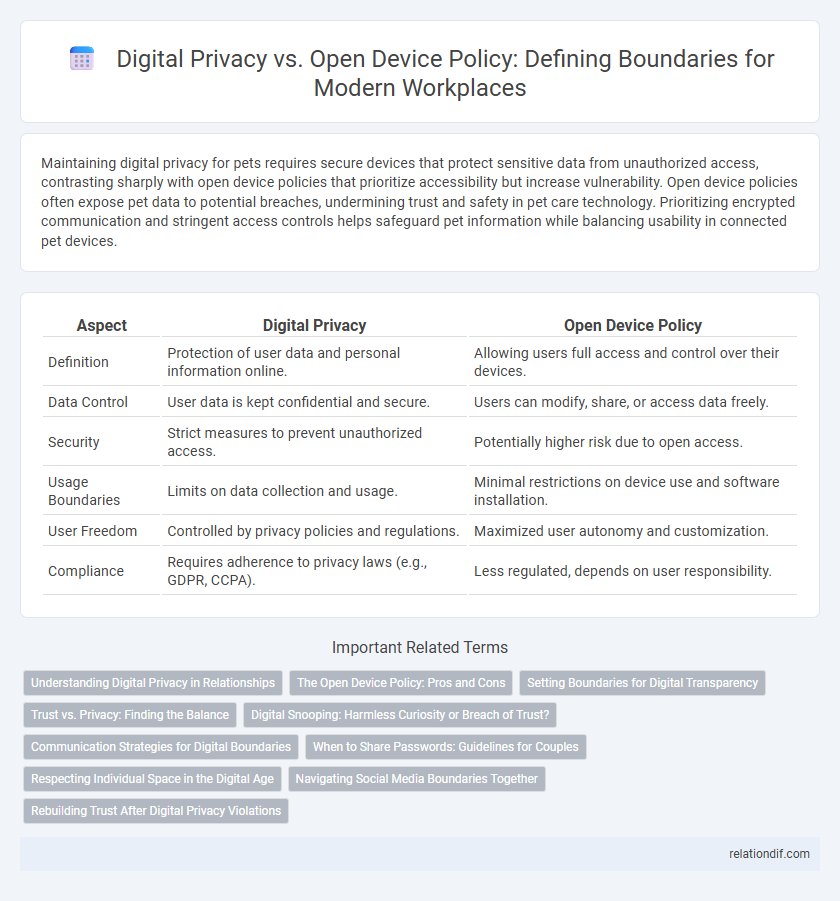
Maintaining digital privacy for pets requires secure devices that protect sensitive data from unauthorized access, contrasting sharply with open device policies that prioritize accessibility but increase vulnerability. Open device policies often expose pet data to potential breaches, undermining trust and safety in pet care technology. Prioritizing encrypted communication and stringent access controls helps safeguard pet information while balancing usability in connected pet devices.
Table of Comparison
| Aspect | Digital Privacy | Open Device Policy |
|---|---|---|
| Definition | Protection of user data and personal information online. | Allowing users full access and control over their devices. |
| Data Control | User data is kept confidential and secure. | Users can modify, share, or access data freely. |
| Security | Strict measures to prevent unauthorized access. | Potentially higher risk due to open access. |
| Usage Boundaries | Limits on data collection and usage. | Minimal restrictions on device use and software installation. |
| User Freedom | Controlled by privacy policies and regulations. | Maximized user autonomy and customization. |
| Compliance | Requires adherence to privacy laws (e.g., GDPR, CCPA). | Less regulated, depends on user responsibility. |
Understanding Digital Privacy in Relationships
Understanding digital privacy in relationships involves respecting personal boundaries around device access and online activity. Open device policies can foster trust but may also blur individual privacy, making clear communication about limits essential. Prioritizing digital privacy supports emotional security and mutual respect in intimate connections.
The Open Device Policy: Pros and Cons
The Open Device Policy allows employees to use personal devices for work, enhancing flexibility and productivity while reducing company hardware costs. However, this approach can expose sensitive data to security risks, complicating IT management and increasing the likelihood of data breaches. Implementing strong access controls and robust endpoint security solutions is essential to balance convenience with digital privacy protections.
Setting Boundaries for Digital Transparency
Setting boundaries for digital transparency is crucial to balancing privacy and openness within an open device policy. Clearly defining access levels and monitoring protocols helps protect sensitive user data while maintaining necessary transparency for security and collaboration. Implementing robust consent mechanisms and encryption safeguards ensures that transparency does not compromise personal or organizational privacy.
Trust vs. Privacy: Finding the Balance
Establishing clear boundaries between digital privacy and open device policies requires balancing organizational trust with individual privacy rights. Companies that implement open device policies must enforce strict data security measures to safeguard sensitive information while maintaining transparency in monitoring practices. Prioritizing user consent and anonymized data collection enhances trust without compromising privacy in collaborative or bring-your-own-device (BYOD) environments.
Digital Snooping: Harmless Curiosity or Breach of Trust?
Digital snooping through open device policies raises significant concerns about privacy violations and the erosion of trust in personal and professional relationships. While some argue that accessing devices without explicit consent is merely harmless curiosity, it often undermines boundaries and exposes sensitive information, leading to ethical and legal implications. Establishing clear guidelines and respecting digital privacy are essential to maintaining trust and protecting individuals from unauthorized surveillance or data misuse.
Communication Strategies for Digital Boundaries
Effective communication strategies for digital boundaries involve clearly articulating expectations regarding privacy and device use within both personal and professional relationships. Establishing transparent guidelines about data access, sharing limits, and response times helps maintain trust while respecting individual digital privacy. Encouraging open dialogue about comfort levels with device sharing creates a balanced environment between digital privacy rights and open device policies.
When to Share Passwords: Guidelines for Couples
Couples should establish clear boundaries for sharing passwords to protect digital privacy while fostering trust. Sharing passwords can be appropriate during moments of mutual consent, emergency situations, or when accessing joint accounts for practical purposes. Maintaining open communication about digital boundaries helps ensure privacy is respected without compromising transparency in the relationship.
Respecting Individual Space in the Digital Age
Respecting individual space in the digital age requires balancing digital privacy with open device policies, ensuring users maintain control over their personal information and digital interactions. Implementing clear boundaries through encrypted data, user consent protocols, and selective access permissions protects personal privacy while enabling necessary device functionality. Prioritizing digital autonomy fosters trust and security, preventing unauthorized surveillance and data misuse in increasingly interconnected environments.
Navigating Social Media Boundaries Together
Navigating social media boundaries requires clear communication about digital privacy preferences within device-sharing environments, balancing open device policies with respect for personal data. Establishing mutually agreed-upon rules can prevent unauthorized access and maintain trust while promoting transparency in online interactions. Encouraging regular conversations about privacy settings and content sharing empowers all users to define their comfort zones collaboratively.
Rebuilding Trust After Digital Privacy Violations
Rebuilding trust after digital privacy violations requires transparent communication and robust data protection measures. Implementing strict access controls and regularly auditing devices under an open device policy helps restore user confidence. Prioritizing user consent and privacy settings enhances accountability and reinforces boundaries between personal data and organizational access.
Digital privacy vs open device policy Infographic
 relationdif.com
relationdif.com